The core of JSVMP (Virtual Machine based code Protection for JavaScript) lies in incorporating code virtualization into the process of protecting JavaScript code. It achieves the virtualization of the source code through JS encryption, transforming the target JS-encrypted code into custom bytecode. These bytecode instructions can only be recognized by specific interpreters, effectively concealing the critical logic of the target code.
Previous article:Analysis of JS Virtualization
Leveraging WebAssembly Technology with JS Encryption for Specialized Virtual Interpreters and Compiling to Conceal Execution Logic: Illustration of JavaScript Code Virtualization Protection Framework.

Implementing Different Virtualization Strategies for Different Types of Target Code: JSVMP Research Process Description
(1) Designing JavaScript Code Virtualization Methods
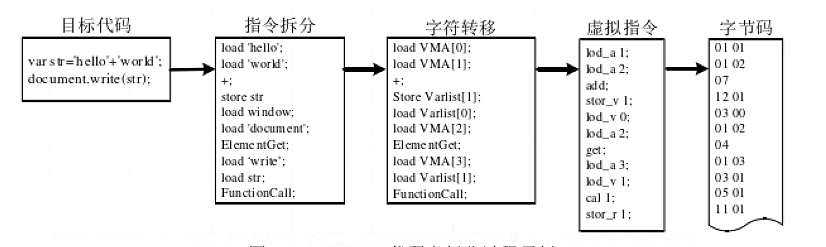
Based on abstract syntax tree, the target code is divided into atomic operations that simulate local execution environments, breaking down the original high-level syntax expressions. For general JavaScript code that involves Document Object Model (DOM) object operations, the attribute names and strings are replaced with array elements through instruction splitting, undergo character escaping, and intermediate code is extracted. A custom virtual instruction set is designed to map the intermediate code to virtual instructions, which are then encoded into bytecode programs according to the corresponding encoding rules.
(2) Designing a WebAssembly-based Virtual Interpreter
Building upon the design of the virtual instruction set, the corresponding interpreter handlers and other important components are designed and implemented. A virtual interpreter scheduling structure is designed to simulate local execution environments with registers, stack, and local dispatching processes. Due to the special nature of object operations, inline JavaScript code is used in C code to implement the corresponding handler operations. Finally, the logic of the implemented virtual interpreter code is compiled to obtain a complete virtual interpreter module.
(3) Designing Virtualization Protection Process for Compute-Intensive Target Code
For a small number of compute-intensive target codes, instruction splitting is performed directly on the abstract syntax tree to extract atomic operations and complete the code virtualization process. Since object operations are not involved, the handler components of the virtual interpreter can be fully implemented in C, and the virtual interpreter is ultimately compiled into a complete WebAssembly (WASM) module, eliminating performance overhead and additional space consumption caused by interaction with JavaScript and additional glue code.
Virtualization of JS Code
Translation: Traditional code virtualization protection targets native instructions, which naturally possess basic operation characteristics. Unlike traditional compiled programs, JavaScript applications are textual code with syntactic attributes and do not inherently possess the atomic nature of native operation instructions. Therefore, the key challenge in virtualizing and protecting JavaScript code lies in the need to first perform a specialized transformation on the target code, disrupting its readable syntactic attributes, extracting intermediate code with atomic operation characteristics. Only then can corresponding virtual instructions and handler functions be designed, and the virtualization process can be completed through instruction encoding. The following diagram illustrates a simple example of the target code virtualization process, and the detailed processing steps will be described below.
GET JSVMP ENCODE FROM jsvmp.com
