This chapter delves into common JavaScript protection strategies and corresponding attack methods, explaining the principles of code virtualization and examining the feasibility of implementing JavaScript code virtualization protection using WebAssembly in real-world applications. As the interactive front-end of a website, web front-end applications primarily rely on JavaScript, so the term "front-end code" in this context mainly refers to JavaScript scripts.
Code Protection (JSJIAMI) Techniques and WebAssembly
- JavaScript Code Protection and Attacks In web environments, JavaScript scripts are transmitted as source code, leaving crucial application logic unprotected against malicious users. In the front-end security ecosystem, exposed data collection and identification logic can be easily bypassed through forged data. Common protection methods include code minification, JSEncrypt, and obfuscation to increase the difficulty for malicious users to understand, analyze, and replicate. This section analyzes these protection methods and corresponding attack techniques.
1.1 Code Minification and Formatting In the early stages of front-end development, JavaScript code minification emerged to reduce script size and accelerate transmission and loading speeds. This led to various compression tools, such as Google Closure Compiler[4], YUI Compressor[35], and UglifyJS[36]. Minified code not only speeds up transmission but also becomes harder to read. As this protection method is simple and doesn't affect source code functionality, most JavaScript code is minified upon release.
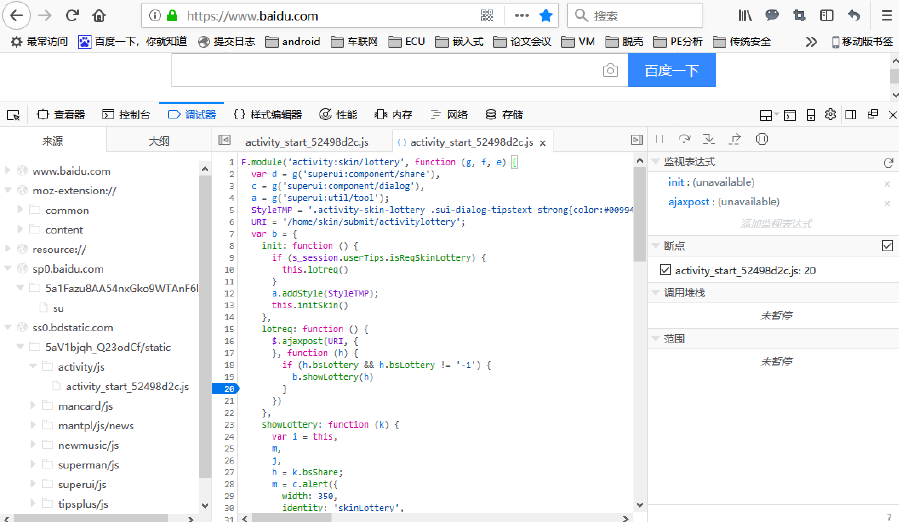
Minification techniques include variable name simplification, replacing semantic variable names with simple characters, merging redundant variable declarations, removing comments and meaningless whitespace or line breaks, eliminating or simplifying optional symbols, deleting dead code, and shortening statements. Due to its simplicity, protected code is easily restored. Most browsers have built-in debuggers with script formatting features. Figure 2 demonstrates the formatted code in FireFox's debugging window; clicking the "{}" button beautifies code formatting by auto-completing spaces, line breaks, and indentation, making the source code readable. Debuggers can also perform complex operations like variable monitoring, breakpoint tracking, and performance monitoring. Tools like jsbeautifier[37] specialize in script code formatting.
During the minification process, Raychev et al. [38] proposed a learning-based deobfuscation tool called JSNice. By analyzing a large number of open-source codes, they learned naming and typing patterns to build a prediction engine, addressing two problems in JavaScript deobfuscation: predicting identifier names (syntax) and predicting variable type annotations (semantics). Experimental results show that 63% of identifier names can be accurately restored, and the correctness rate for variable type annotations reaches 81%.
1.2 Code JSEncrypt and Decryption Similar to binary program protection, JSEncrypt is often used to hide target code semantics in the JavaScript code security ecosystem. The main idea of JavaScript code encryption is to use an encryption method to convert target code into a meaningless string of characters, embedding a decryption module in the script. When executed in the browser, the decryption module restores the source code. Since the decrypted result is a string and not a valid browser-executable script, APIs such as "eval" and "Function constructor" are used to decode the source code string and execute the JavaScript logic.
Analyzing the code JSEncrypt protection process reveals that JSEncrypt script files require a decryption module, and regardless of form, they ultimately rely on and call methods like "eval" to execute decrypted logic. Therefore, code JSEncrypt features are apparent and easily restored. Attackers don't need to analyze JSEncrypt details; they only need to intercept the final "eval" call, change it to print output strings, and obtain the decrypted source code. Figure 3 provides an example of the JSEncrypt and decryption process. The JSEncrypt JavaScript code segment is confusing and difficult to understand, but by modifying the target code's "eval" call to "console.log" and outputting it in the browser's debugging window, the source code can be easily obtained.
eval(function(p,a,c,k,e,r){e=String;if(!''.replace(/^/,String)){while(c-- )r[c]=k[c]||c;k=[function(e){return r[e]}];e=function(){return'\\w+'};c=1};while(c-- )if(k[c])p=p.replace(new RegExp('\\b'+e(c)+'\\b','g'),k[c]);return p}('0("1, 2 3 4 5 6!");',7,7,'alert|Congratulations|you|got|the|source|code'.split('|'),0,{}))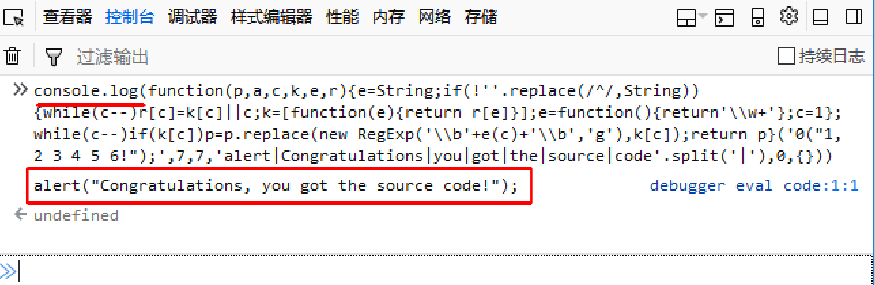
Due to the obvious features of single JSEncrypt methods, which can be easily cracked, a combination of multiple methods is often used to increase protection strength. Unique JSEncrypt approaches, such as hiding JavaScript code in other media using steganography, have been developed. Saumil Shah [39] implemented a program called Stegosploit, which uses a technique called Steganography to hide target information in an image. The author leverages this technology to write target JavaScript code into image pixels. When the image is loaded in a browser, the hidden target code is extracted and decoded using the HTML5 CANVAS element. It's challenging to detect issues within the processed image without careful analysis. However, this method, like general JSEncrypt methods, requires dynamic decoding and execution of the program, making the cracking process similar to attacking general code JSEncrypt .
1.3 Code Obfuscation and Deobfuscation
Code obfuscation is a set of program transformations that hide programming intent while preserving semantics. The primary goal is to reduce target code readability, making it difficult for attackers to understand the program's logic through manual or automated analysis. Code obfuscation can be applied to compiled local code, intermediate code during compilation, and source code. Generally, obfuscation can be categorized into the following types [11]:
(1) Layout obfuscation: Removes code formatting (e.g., spaces, indentation, line breaks), deletes comments, and compresses code to reduce readability and size, similar to code minification.
(2) Name obfuscation: Replaces identifier names (variable names, function names, etc.) in the code with meaningless random names. For example, it's easy to guess that a JavaScript variable declaration statement "var name" is related to a name; if the variable name is replaced with "a", more effort is required to analyze the context and understand its semantics.
(3) Data obfuscation: Typically obfuscates data flow in the program by reusing variables, inlining variables, or JSEncrypt data. For example, using the same identifier names in different namespaces or assigning the same value to multiple random variables can effectively obfuscate data flow direction and increase the difficulty of understanding code logic.
(4) Control flow obfuscation: This method changes the program's control flow. Common techniques include inserting opaque predicates [40] and flattening control flow [41]. Opaque predicates create some conditions that are either always true or false and cannot be inferred during static analysis, only determined at runtime, to increase static program branches and alter target program control flow. Control flow flattening changes the program's hierarchical structure by dividing loops and nested conditional branches into basic code blocks, then using loops and "switch" structures to flatten the program structure, controlling the execution order of basic blocks through "case" value changes. These techniques complicate code control flow, hindering understanding and analysis.
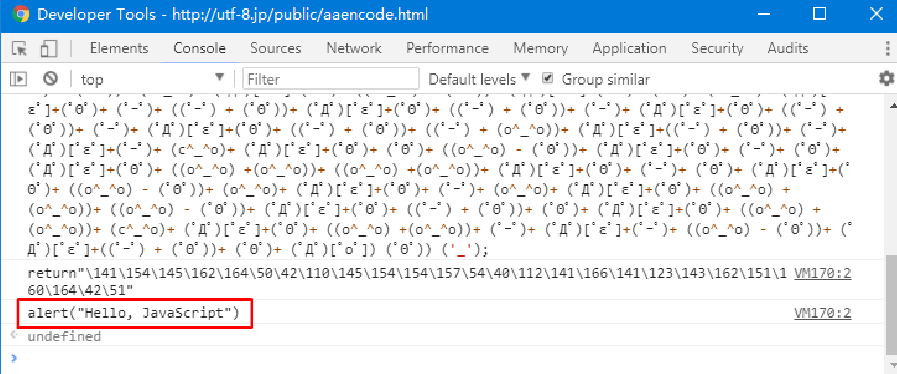
JavaScript obfuscation belongs to source code obfuscation and generally refers to the aforementioned name, data, and control flow obfuscation, which are mainly implemented through modifying the abstract syntax tree (AST). Many protection tools offer JavaScript code obfuscation features, and commercial platforms can provide customized deep obfuscation protection. Notably, some malicious scripts often use obfuscation to hide malicious code and evade security detection [42], leading to research on deobfuscation implementations for commonly used obfuscation protection tools. For example, Metasploit's [43] JavaScript obfuscator is often used for malicious code obfuscation, while as shown in Figure 4 [44], the malicious code deobfuscation tool JSDetox [45] can deobfuscate JavaScript code obfuscated by Metasploit. Etacsufbo [46] is an open-source deobfuscation tool that mainly.
YOU CAN GET ONE KEY JSEncrypt FROM jsvmp.com
