In the field of binary code protection, especially for the protection of PE (Portable Executable) files, JS virtualization has become a mature and reliable technology with a wide range of applications. In this article, we will introduce the basic principles of JS code virtualization and obfuscation.
JS virtualization involves converting executable code into an intermediate form that is difficult to analyze and modify. By transforming code into an intermediate representation and using obfuscation techniques such as code scrambling, control flow flattening, and instruction substitution, it can make it difficult for attackers to understand and modify the code.
In addition, JS virtualization also utilizes anti-debugging techniques to detect and disrupt analysis attempts. This can include modifying the behavior of certain code paths or introducing artificial delays to slow down the analysis process.
Overall, JS virtualization is an effective technique for protecting sensitive code and resources from reverse engineering and other malicious attacks. Its use of obfuscation and anti-debugging techniques makes it difficult for attackers to analyze and modify the code, providing reliable protection for your PE files.
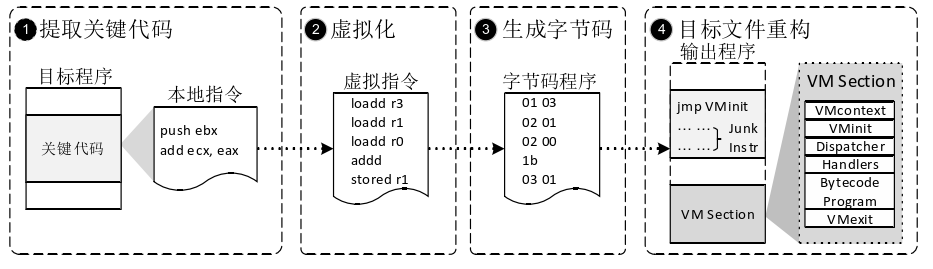
JS virtualization protection involves using a virtual instruction set and interpreter to encode executable code into special bytecodes for protection. The virtual interpreter consists of several important components, including VMContext (Virtual Machine Context), VMInit (Virtual Environment Initialization Module), VMExit (Virtual Machine Exit Module), Dispatcher, and Handler (Bytecode Interpreter).
By using a virtual instruction set, the intermediate language used in the protection process does not affect the real local environment, including the values of general and flag registers. Thus, a virtual environment VMContext is established to record the execution process, which contains a group of virtual registers corresponding to local registers. When entering the virtual machine, the VMInit module is responsible for initialization and mapping of the local environment to the virtual environment. When exiting the virtual machine, the VMExit module maps the register information in the virtual environment to the local real environment, restoring the local execution context. During execution, the virtual interpreter's scheduling core Dispatcher loops through the bytecodes and schedules the corresponding Handler to interpret the semantic target function contained in the bytecode.
WebAssembly is a feasible technology for implementing JS virtualization in JavaScript protection. Popular browsers such as Chrome, Firefox, Edge, and Safari have supported WebAssembly and its primary advantage is its ability to greatly improve JavaScript performance. As a result, WebAssembly is widely used in browser-based applications, game development, and other performance-critical web-based tools.
Existing JavaScript protection solutions are limited because the source code is easily readable and understandable. Attackers can easily analyze and remove the key protection logic. However, JS virtualization protection changes the target code to custom bytecodes, which can break the syntax properties of the text and hide the key logic. Its virtual interpreter can dynamically restore the logic during execution, making it difficult for attackers to remove key structures to bypass protection. Moreover, if the interpreter module's security is compromised, attackers can track and extract the critical mapping rules. Therefore, the virtual interpreter's core logic is implemented in C/C++ to ensure security, and then compiled into WebAssembly binary format using the Emscripten framework for loading into the target application.
In conclusion, this article proposes a feasible method for JS virtualization protection based on WebAssembly for both usability and security reasons. While theoretically, content on the client-side is never completely secure, this method greatly improves the security of JavaScript target code compared to having all the code logic directly exposed to users.
YOU CAN GET ONE KEY JSEncrypt FROM jsvmp.com
